Maybe you should store passwords in plaintext.
“Never, ever, think about something else when you should be thinking about the power of incentives.” – Charlie Munger, American billionaire investor.
Okay, you probably shouldn’t store passwords in plaintext, but I’ve met a few who do. They don’t store their own passwords in plaintext and they use a password manager for those things, but they don’t hesitate to store credentials at work in plaintext.
Huh? That’s obviously horrible. What gives?
These people are either a little bit unusual, or maybe normal people are the unusual ones. And they don’t just store work passwords in plaintext, there’s other things as well. I first caught wind of their thinking when having just a gentle conversation about work stuff:
Me: “Yeah, so I saw that our login endpoint had a big security vulnerability. I found it, raised it as a big issue and got a few people together across teams to drive a fix. We had a good celebration over that.”
Them: “Huh? Why did you do that?”
Me: “What do you mean? I found an important problem and drove a fix for it. I think that was really good to do.”
Them: “Oh. Yeah, I mean, I guess. But what did you get out of it? Did they give you a bonus?”
Me: “N..o.. I didn’t get anything, but-“
Them: “So you did a bunch of extra work for nothing then? You’re a chump.”
Are they right? Talking some more with people like this, I’ve come up with a list of opinions they have about their work:
-
One person is aware of almost 100k/mo in unnecessary spend on AWS. They don’t bother to care about it or fix it. They reason that they’ll be punished for fixing it by having to JIRA the issue, bring it into the sprint, discuss it in standup, and not be rewarded with any fraction of those savings financially. Worse yet, it may take longer than expected to fix and they may be punished for it on their performance review. They’ve known about this issue for almost eight months.
-
Another person simply doesn’t care about shipping code with bugs, and maybe even tries to. They get to shirk actual development duties by fixing their own broken code instead, and the fixes are celebrated. Not only that, but their management thinks that their work must be tricky because of the bugs that appear. “I get paid the same whatever it is that I work on, so I’m going to try to keep my work relaxed and easy.” They considered pretending to have very young children so they can opt out of the team’s on-call rotation that gives no extra pay, but thought that was going too far.
-
A third literally has about a hundred diffs stacked up that repair innocuous compiler warnings, and they send one or two of them out when they don’t feel like doing their regular work and claim they “stumbled on some issues and fixed them.” They say they figured this out after their last raise was below inflation, and say their new goal is to be “perfectly mediocre.” They’re now working on a plan to quit their job for a “sudden emergency leave” and then negotiate their rejoining at a proper salary increase in a month. They don’t care too much if that doesn’t work out, because they have a second full-time job.
-
Oh yeah, and all of these people store work credentials in plaintext and don’t care about writing secure code. “A security breach isn’t my problem and avoiding one doesn’t get me anything.”
Now, I would personally feel shame if I did these things. I pride myself on writing good code, on fixing bugs, on shipping things correctly and on time. Seeing bad code frustrates me, and working with bad engineers frustrates me even more. This group of people seem to have been like that at some point in time, and then turned to “misbehaving” in this manner.
“You don’t get rewarded for being extra. You don’t get any money when you save costs. You’re going to get a raise below inflation. You’re stupid for caring the way that you do. The business’ downside risk is not yours, and it’s profits are not yours either.”
I’m not sure I can really come up with a good counter-argument to this, and maybe normal people are all the weird ones for not behaving like this. They’re right in that the incentive structure to perform well.. is missing if you think about it. One person pointed out that the vulnerability I found internally granted me a bonus of $0, whereas if an external researcher found it they’d have been paid a bounty easily in the tens of thousands of dollars. They’re right, and that does sting a little bit.
Is there some way to correct this? How do you reward good behaviour here, and discourage “misbehavior” like this? Not being rewarded with money seems to be the common theme here, but financial incentives are tricky to get correct as evidenced by this Dilbert comic:
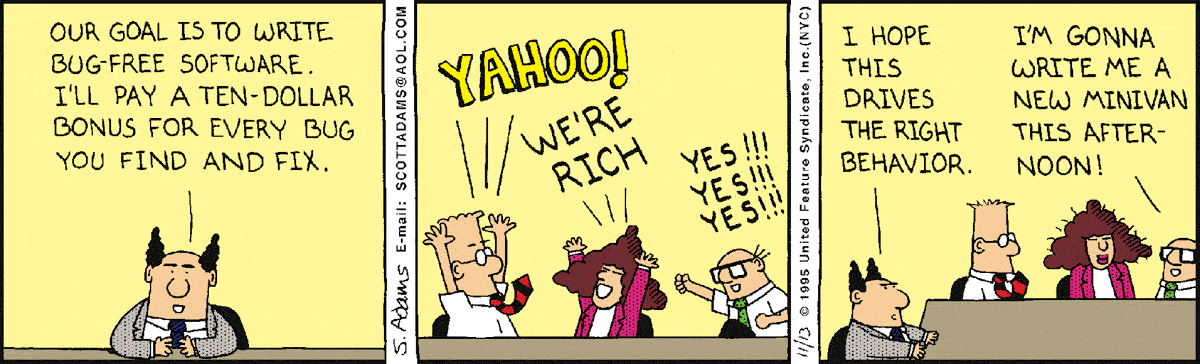
Steve Levitt, American economist and co-author of Freakonomics says to not even bother with financial incentives in this 15-year-old video (4:56 long):
“I think the real answer, the real answer […] this is going to sound weird or bad – is to cajole or trick your employees into thinking that what they’re doing is important.”
Doesn’t that … actually sound weird and bad? I’ve been thinking about this for a while, and maybe I really am a chump but it seems like the system says we should all store our passwords in plaintext too.